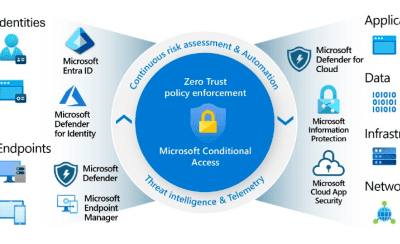
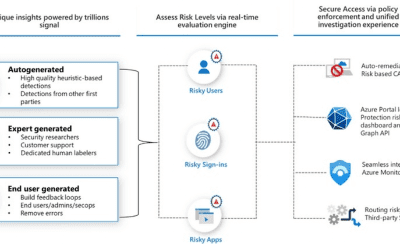
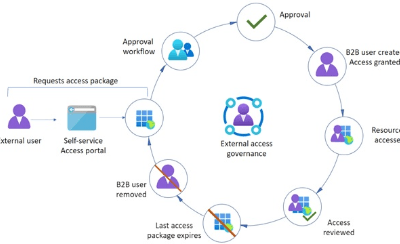
Over the past twenty years, I have built a solid career within the evolving Italian IT companies, working across multiple environments and technologies. My professional journey has been driven by curiosity, precision and a constant search for effective, forward-looking solutions. I have developed an in-depth understanding of enterprise infrastructures and everyday operational challenges.
Beyond the technical domain, I greatly value the human side of IT, such as collaboration, mentoring, and knowledge sharing. Recently, I had the opportunity to serve as a trainer for a course on Cloud Computing and Manufacturing, teaching a class of 25 students about the real-world applications of cloud technologies. That experience inspired me to create this blog, where I share insights, scripts, and reflections about technology, security, and the practical side of IT operations
For privacy reasons and to respect the company who I working for, I have chosen do not disclose the name of my last employer in the work experience section on LinkedIn profile. Please don't trust other sites that show my CV. I invite you to refer only to my LinkedIn profile for additional details, including references and further information about my professional background. CheckMe